Safe authorization
MQTT IoT Suite uses a security authentication policy for access authentication, that is, access authentication is based on tokens computed by core secret keys.
Security Authentication Policy
The security authentication policy mainly ensures access security in the following ways:
Avoiding direct network transmission of core secret keys to protect core secret keys over the network.
Performing identity authentication using a token signed with irreversible algorithms, so even if this token is stolen, the attacker cannot obtain core secret keys through token reversal.
Authentication parameter token characterized by user-defined expiration time, which can mitigate the risk of attack/counterfeit from the viewpoint of time dimension.
Common Security Solutions
Solution 1
Visitor (application or device) solidifies an access key into software. When a service access is needed, the key is used to calculate temporary token, and then this temporary token is used to authenticate the service access.
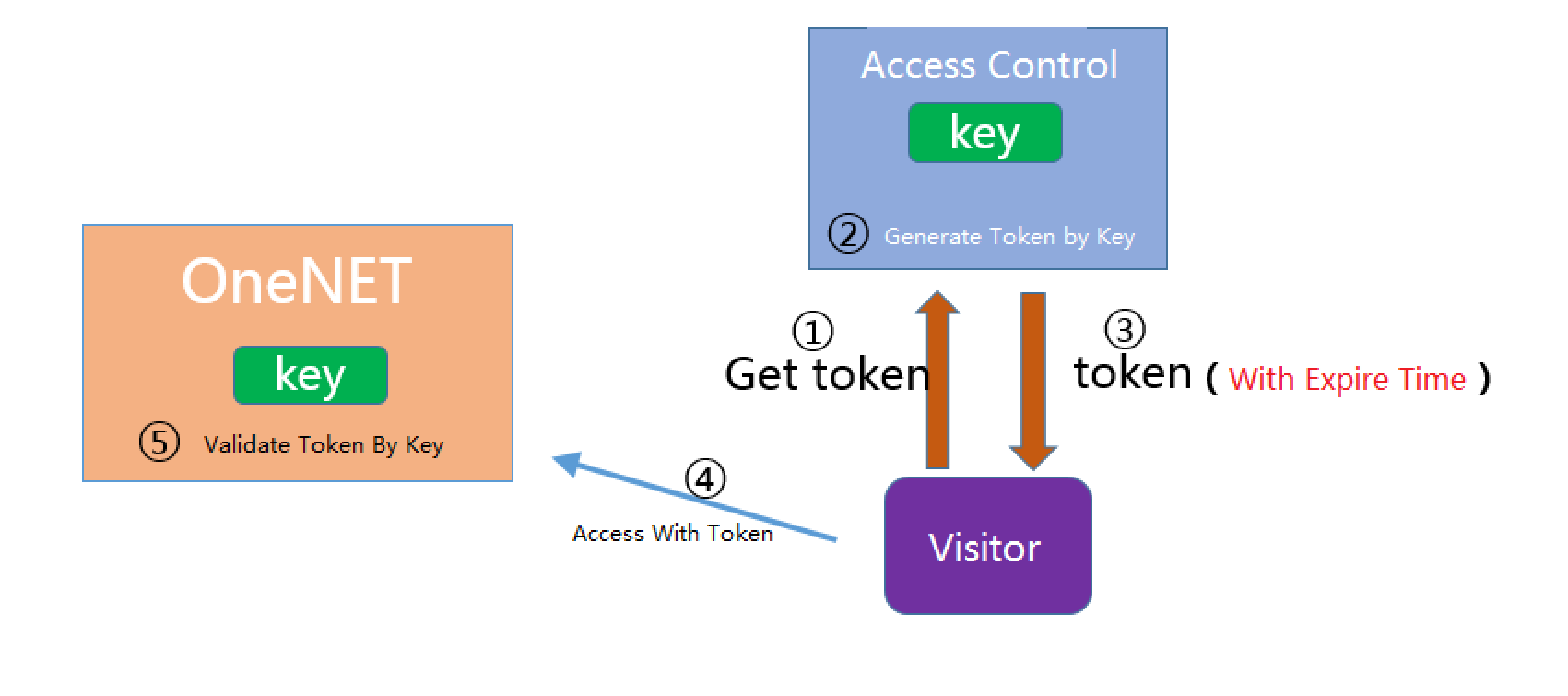
Solution 2
First of all, visitor has to get a temporary access token from the Access Administrator which can customize the validity period
(i.e. expiration time) of the token as needed, before accessing the OneNET platform.
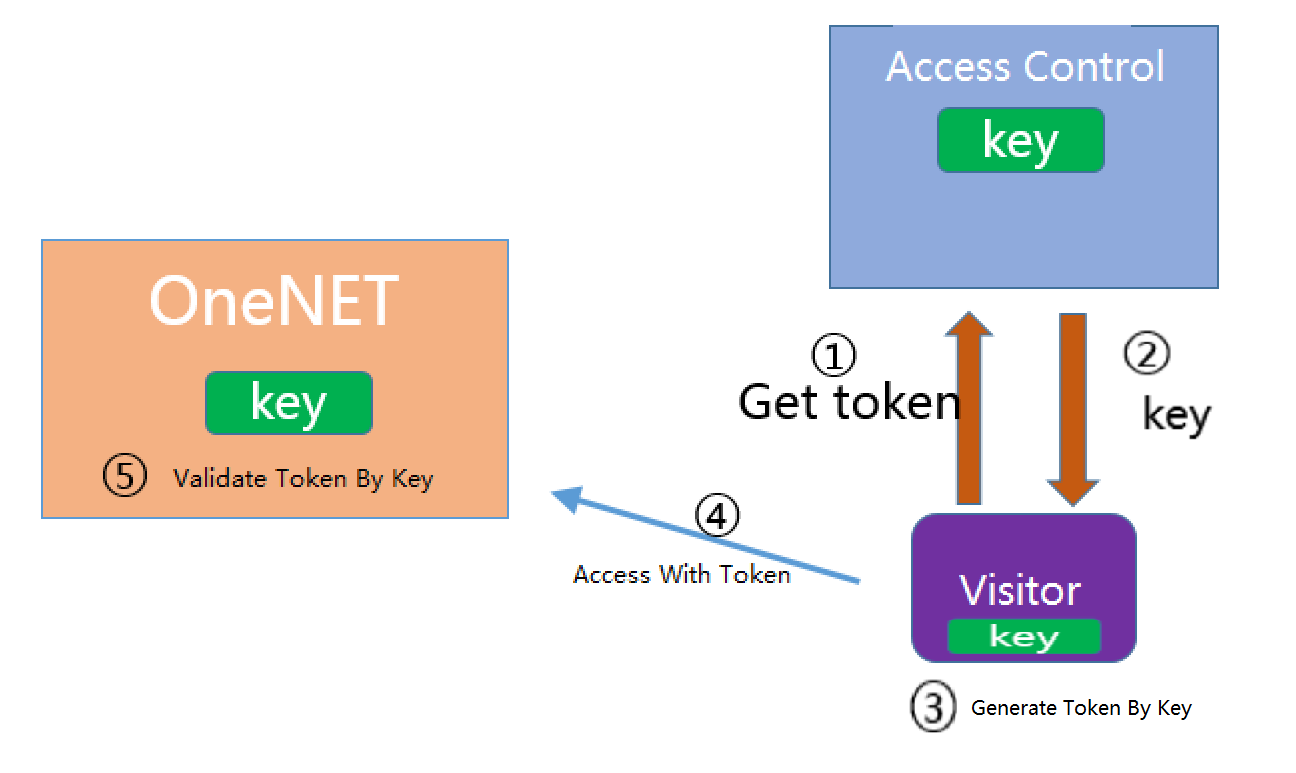
Solution 3
The Access Administrator directly authorizes key to visitors (for example, directly burns key into the device), and then the visitor generates an access token using the key.